The Art of Cyber War and Cyber Battle: Formations
- Brandon Hitzel
- Jul 7, 2019
- 10 min read
Updated: Aug 10, 2019
This post abstractly looks at the relations of some ancient and modern battle formations and applies them to the cyber domain. How would you describe your network formation?
The Art of Cyber War and Cyber Battle is a blog series where I look at physical domain warfare and the cyber domain in order to compare and discuss differences, similarities, strategies and other related topics. This doesn't mean it's a straight physical to technical translation and that we won't look at things like strategic philosophy or specific tactics. If you haven't read it here is the series introduction. Formations is the topic of one of the chapters in the book The Art of War by Sun Tzu.
So I was deep in a game of Rome Total War 2 when I started thinking about the different ancient land army formations and how it related to something like a network topology or the framework for information technology teams. In the physical domain it's very important to see how your opponents forces are deployed and what their unit composition is to ensure your unit's capabilities are aligned to counter and overcome them. Yet in the cyber domain the attacker is generally formless and makes efforts to hide their identities while the defense is a fairly standard form (think of the typical enterprise network topology). Although this contrast exists the objectives in each domain remain the same - deploy your resources in a matter that is advantageous to yourself.
Pretty much any organized body looking to accomplish an objective is generally structured in a certain way. The first example that comes to mind is probably something like the chain of command which can be seen universally in global corporations and armed forces; however, I want to look at some specific historical and modern examples of military formations and relate them to networks and IT teams.
Armies would organize into certain formations on the battlefield based on the situation or the terrain. There's larger/broader strategic formations and also a smaller tactical formations. Each could look like a line, an echelon, a square, a wedge (beyond scope of this post). At the basic level these could apply to a modern squad of 4 tanks or planes or groups of soldiers. The armed forces of antiquity generally met each other in variations of lines a couple miles long on open fields or plains etc. Strategically you're looking at the larger picture with higher level decisions, whereas tactically you're looking more precisely - we'll be looking somewhere in between.
The formation chapter in The Art of War doesn't discuss actual form or deployment, but more about of the philosophy of achieving victory by measuring and assessing your opponent for their form. It talks of restraint in revealing your form while identifying the weaknesses in your foe. We won't be getting too philosophical here as you could create hours of content on this subject alone, so I will focus more on some specific connections.
House keeping note: Generally a military will have small units and then combine them to increase unit size with the smallest starting at fire teams (2-3), squads (5-10 persons), then a platoon (30-40), then company, battalions, divisions (5000+) etc. then comparable in business you'd have like a work group (3-6), teams (10-15), departments, divisions, organizations... so forth and so on. The way the formation will looks will depend on the terrain (e.g. mountains, rivers, IP routing) or the specialty of the unit or team (e.g. desktop, SOC, air defense, infantry).
A classic example
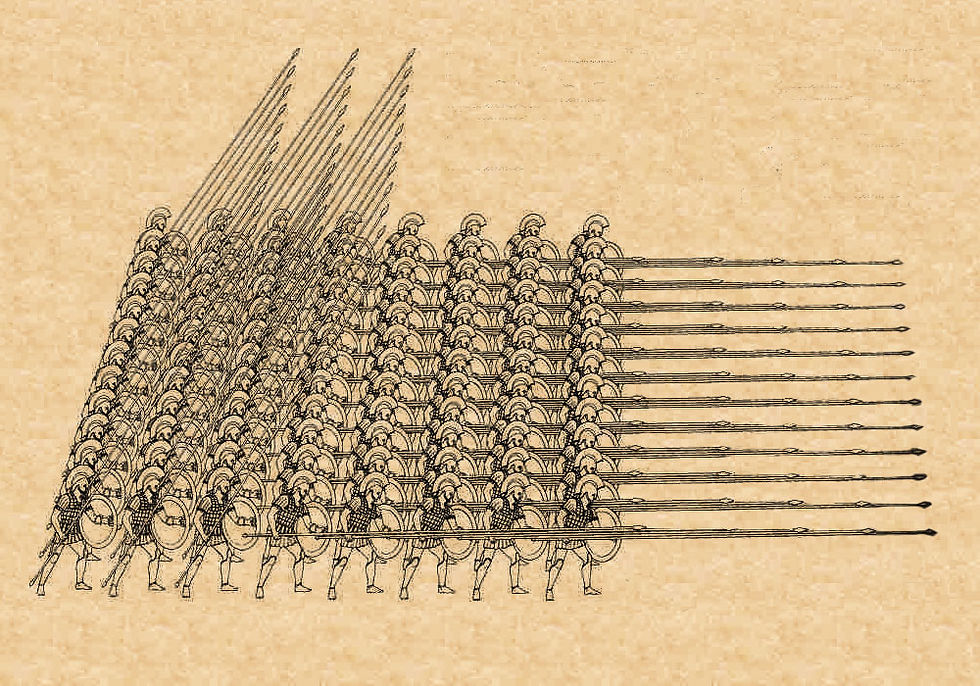
The Greek Phalanx (pictured above) was one of early military formations which was proven time and again in ancient battles to be effective. The Greeks used it against the Romans, the Persians, and also to conquer most of their known world. The phalanx was deadly from the front with densely packed soldiers each holding a long spear and shield which meant it could seldomly be overcome in a head to head match up. The tight grouping and cohesion of the phalanx was a pro because of it's frontal capabilities and a con because it was slow to move and not very maneuverable. For example if the formation encountered rough terrain or had to turn the grouping would space out and become susceptible to breakage.
Additionally the formation was vulnerable from the sides or Flanks. Generally the more mobile horse mounted cavalry would cover the flanks of the formation so the slow moving spear infantry could hit the enemy troops head on where the phalanx was strongest.
One of the most famous battles where the phalanx was "out flanked" or the enemy was able to get behind the formation and exploit its vulnerabilities was Cynoscephalae. Basically the Greeks were defeated by the Romans because the Roman cohort formations were more flexible and mobile. Long story short, the Greek left side of the battle line was pushing the Romans back, however the Romans were able to advance up hill faster on the right of the front line before the phalanx could form up properly at the top. Consequently the Romans were eventually able to get behind the Greek left front line and eventually cause a retreat.
Jumping back to the cyber domain I'm sure you are familiar with the basic network defense for the majority of homes and S/M businesses - the single firewall with nothing else. I see this setup like the phalanx, it's very hard or impossible to actually penetrate a properly configured stateful firewall head on (vulnerabilities aside), but if you can get around to the flanks then the liabilities become apparent. The ways an attacker could flank your defense is with phishing e-mails, malware downloads, or openings in the front (like when the phalanx would hit uneven terrain). When the aggressor gains access into the network then your formation has been outflanked.

That is why coverage of the sides of the formation is important like the cavalry deployed on the flanks of armies in previous centuries. In my opinion, network flank protection can be achieved with auxiliary services or hardware like end point anti-virus, e-mail security, URL filtering, threat detection and other types of hardware like proxies. If a trojan gets past the firewall hopefully your A/V will catch and stop it, or that phishing e-mail won't even make it into the inbox due to the filtering service that was purchased. With all the malicious scanning on the internet, having things like destination NAT, port forwarding, and reverse tunnels can be dangerous for your network as bad actors can find and exploit these - basically finding a gap in the front to exploit or breaking the front line's cohesion so to speak.
3 tier structure
How is your support department or xyz IT team structured? Typically some IT departments are structured in way to have a basic composition like tier 1 for basic tasks, then more advanced technicians at tier 2 to solve the majority of issues, and then finally a tier 3 engineering group to take the advanced trouble tickets and projects.
The tier 1 could be a help desk to handle very easy issues or they could be a pre-tier 1 who triages tickets out to different groups like security, desktop, telephone etc. After they become more skilled they might advance to tier 2 and so on.
I like this system because it provides flexibility and enables the ability to handle high volumes of work or incidents by sharing the load.
What's interesting is tiered systems were seen thousands of years ago when the Romans developed the Triplex Acies formation (triple battle order) which had 3 infantry lines and a forward deployment of light skirmishers. The front skirmishers were called Velites, they would "screen" or cover the larger army as they formed up and were younger more inexperienced soldiers. these troops were the first to contact the enemy to prove themselves (i.e. helpdesk). The next basically first line of true infantry were the Hastati, then behind them were the more experienced and equipped Principes, and finally the most skilled and seasoned troops - the Triarii.
The history books tell us they were typically aligned in a checkerboard layout vs a straight line so they could easily support one another and rotate forward/backward as they engaged the enemy forces to prevent fatigue. Also each of the various types of infantry had different equipment, for example the Hastati might have a spear but were considered swordmans whereas the Triarii were more similar to a phalanx with long spears. Just like how different IT specialties use different tools and software. For instance a wireless engineer will probably be using a wireless survey device.
This battle formation was very successful against both capable and unorganized opponents who might have had similar force composition but were not as disciplined or trained. Later the Romans developed a more standardized methodology where all the soldiers were essentially the same unlike the differences seen in the Triplex Acies.
The point I'm getting to here is to think about how your support department/team/system is setup. Think about where the strengths and weaknesses are. Before the triple battle order the Romans used a system very similar to the linear phalanx lines but over time they realized changes were needed to stay ahead of their adversaries. Therefore, it would be wise to assess one's formation so to speak in order to determine if any changes are needed.

Thinking of enterprises - Is the mean time to resolution very long? Then perhaps you need to add an addition tier of more experienced engineers. Moreover, maybe your network needs a lot of improvements or there is a new refresh initiative but progress is really slow, therefore a tier of technicians likely needs to be leveraged to help spread the work to allow engineering projects.
What does your security team look like? Is the incident response team under-utilized? Perhaps you need to improve alerting automation or add more analysts. Furthermore, thinking of the attack side of house - maybe there needs to be more screening by "front line skirmishers" so the target APT competitor cannot ascertain your particular group's intentions.
In my opinion the tiered system is good because it allows progression of skill, sharing of work, and implements more subject matter experts (SME). However not every department is able to be structured this way.
Is your team more like the phalanx? Only able to handle 1 type of task head on? In that case it would be prudent to have everyone on the team trained with sister domains or cross-trained within the department in order to improve cohesion and flexibility. Moreover, in another scenario maybe there is only 1 type of specialty on the team which I would think means you would have tiers 1,2,3 based on skill level and seniority to handle different tasks.
Although there are a ton of other factors keep in mind that if the team is not structured properly then they could easily fail to achieve their attack objectives or conceivably break down in the response to a security incident or priority ticket (e.g. overwhelmed with security issues or tickets) - just as the Romans unorganized foes did many times (but not every time!).
A Modern look
Fast forwarding to modern times. Although in ancient armies we saw different types of units like archers (bow and arrow), horse cavalry, adn foot soldiers, the modern unit composition is more diverse and covers a wider range of objectives. An example from the modern physical domain would consist of a reconnaissance unit, an infantry unit, an armored unit, helicopters, air defense, intelligence, support etc. (also just want to add the united states army now has tactical cyber units ). Based on the unit's role determines where it would actually be in the division's formation versus previous examples where the unit's arrangement was replicated and pre-determined before battle.
Therefore sometimes it's best to structure a team based on the specialization and it's something you probably have encountered before. I do like this approach as it theoretically enables higher quality results by SMEs (i.e. experts focusing on what they do best).

This picture depicts the deployment of some of the previously listed modern assets in a manner based on the role. This is obviously placing each unit based on a simple characterization but you probably notice some familiar things to hone in on. Perhaps the forward reconnaissance units looking to identify the objective's strong and weak points just like someone doing Nmap scanning or having bots scanning subnets - an important first step in the cyber attack chain.
Then there are the armored tanks holding the main roads intersection, just like how you might place intrusion prevention devices (IPS) on your main circuits and routing paths in the network. Moreover, the Attack helicopters watching the flank like ancient cavalry or providing quick support to priority incidents like a Computer Security Incident Response Team (CSIRT) or tier 3 engineering escalation team. These are just some similarities worth mentioning.
Quotes
Blue team:
"When you have assessed the opponent and seen the opponent's formation, then you can tell who will win. If the opponent is inscrutable and formless, then you cannot presume victory"
- Du You, commenting on Sun Tzu from The Art of War.
I translate this in that often the red team is formless or the identity is unknown, consequently one cannot assume victory based on that you have X device in the environment or knowledge of X technology (i.e. pre-battle formation). Thus, you need adequate threat intelligence in order to ascertain the form of your adversary and the attack type to develop the right countermeasure.
Red Team:
"Secret plotting and covert operations seize victory in formlessness - no one hears of the knowledge that assesses opponents and ensures victory, no one sees the success of those who take the flag and assassinate the generals. The way to be able to win without fail is to see when opponents are in vulnerable formations, and then disposition your forces to prevail over them."
- Zhang Yu, commenting on Sun Tzu from The Art of War.
This one is pretty self explanatory, it echos the philosophy of locate the enemy weakness and employ your resources in a manner that will exploit that vulnerability. I also think the quote related to the red team because it mentions secret plotting and covert operations and how there are many successful tactics that remain hidden - just like hacks and data breaches that aren't yet known or will remain unknown.
Conclusion
With the lessons learned over time from victories and defeats, along with the evolution of technology, military formations have changed. There are examples in history where a formation provided an edge for victory to a numerically inferior force which illustrates it's importance (saving that for a future post). The structure and deployment of your hardware and personnel is important to provide a adequate response to the challenges and attacks/defenses you face.
We can see how similarities can be drawn between the physical domain to the digital arena and how the philosophy carries over - even if it was from over 2,000 years ago. With the advent of the cyber domain you can be sure there will be continual development in this area.
I hope this post exercised your imagination a bit and provided a different perspective on things along with helping to educate and entertain.
Deeper reading - non-technical:















Hi Brandon!
I loved your article, which I came across while doing some research related to my dissertation. I was wondering if I could discuss more on how The Art of War and other texts (which I can discuss in private) can help us understand the designs of malware and it's attacks, and how these methods can show us ways to reverse engineer it (or in other words, how to defend ourselves or how to fight back against it).
Do let me know if you would be interested in taking this discussion further. My email is vera(underscore)morgana(at)hotmail(dot)com.
Thank you!